Backing up your data is easy and secure on Android. But there are some issues with the service that Google needs to sort out.
I love seeing headlines about encryption hit a news cycle. Anything that gets a person more aware of their options when it comes to making sure that they are the only person with access to their data is important. So important, in fact, that Google does it by default with your backed-up data.
Mostly. Google does offer a complete end-to-end encryption service and the company uses it for the data in its own Android apps and your phone settings since Android 9 Pie. It's on by default, you don't have to do anything except check the box that you want to use the service when you set up or restore a phone.
But no service is perfect, and Google's backup does leave a lot to be desired.
What is end-to-end encryption?
End-to-end encryption means that only the person who created the data and the person who is supposed to receive the data (which can both be the same person) can supply the credentials to access encrypted data.
Sometimes, that means a password. Sometimes it means an app you have authorized to decrypt data received on your behalf. Sometimes it means a secure lock screen. But it always means that no person or server or company in the chain has access. Only the sender and the receiver.
Only the person at each end has the key, thus end-to-end.
In the case of Google's backup service, it means that you have a secure lock screen and have used it to unlock your phone. While your phone is unlocked you can create and send data as well as receive encrypted data. Most every Android phone has some sort of secure element that allows actual hardware to encrypt and decrypt on the fly using a token generated by a combination of your Google account password and your lock screen security.
On Google hardware — that means both Pixel phones and servers that hold the data — it's called the Titan Security Module. You feed it the information it needs to make sure that you are really you and your data is backed up and can be retrieved, but only through the Titan module. Google nor the Titan module itself know any password to decrypt your data, only you do.
More: Apple may have ditched encrypted backups, but Google hasn't
How does it work with Android?
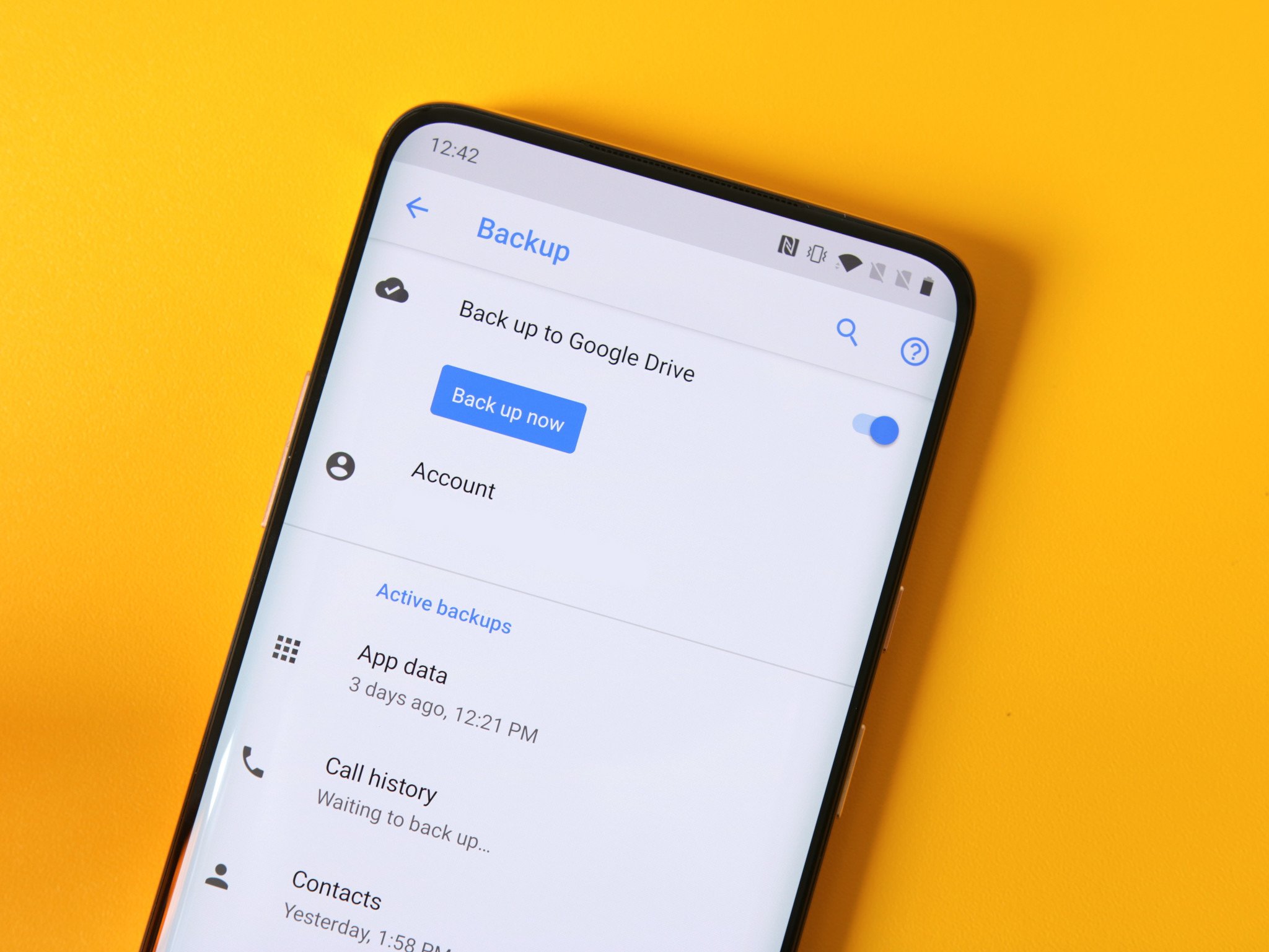
When you're setting up a new phone running Android Pie or later, you come to a section during setup about data backups. It reads:
Easily restore your data or switch phones at any time. Your backup includes apps, app data, call history, contacts, device settings (including Wi-Fi passwords and permissions), and SMS.
Your backups are uploaded to Google and encrypted using your Google Account password. For some data, your device's screen lock PIN, pattern, or password is also used for encryption.
App data can be any data that an app has saved (based on developer settings), including data such as contacts, messages, and photos.
Backup data will not count toward your Drive Storage quota.
You can turn this service off in Settings.
If you choose to enable this (and you should since even Google has no access to it), at least once per day all your preferences and associated application data is packaged up, encrypted with a backup key, and stored in a hidden area of your Google Drive account.
New data can overwrite older data, and in some cases, it's not necessary to back everything up. Google Calendar is a good example; your preferences and settings are backed up but the actual calendar data is stored in the cloud and won't be included in the backup package.
Backed up data is saved to a hidden spot in your Google Drive account.
For other things like your SMS messages, any new data from new messages is appended to the existing data, and your preferences and settings are still saved.
Basically, everything needed to make a brand new phone work just like your old phone is saved in your Drive space. But only if the developer included it in their app.
Where things need to get better
Google wants everyone to use Android. That means it can be pretty lax when it comes to enforcing "best practices." We see it happen with companies making phones, companies who are data service providers, and with app developers. There is a right way, but Google doesn't force anyone to always do the right thing.
That means that your backup probably won't be as complete as you would like.
When you restore from a backup, all of your apps are automatically downloaded (because the Google Play app and the device settings are correctly backed up) and then any backed up data for those apps is put in the right place. But if an app never backed up its data in the first place it will be like it was when you first downloaded it.
Developers aren't forced to employ Google's Android Backup service.
We've all seen this with games. Some games use Google's backup service and you can reinstall them and pick up right where you left off. Others don't and you have to start fresh. Third-party messaging clients can be the same way. And these two cases are the ones we want backed-up the most.
While iCloud backups aren't end-to-end encrypted, at least backing up preferences and data is mandatory. If you want your app in Apple's App Store, you follow all the rules. Google could do the same, especially since it has made things super-easy to implement the backup service. Audit Google Play and force developers to make sure all their apps use it, and we benefit.
There also needs to be a way to opt-out of end-to-end encryption. Right now, if you turn the backup service off everything is gone. It will all go back in place if you turn it on again, but there is only one option — yes to end-to-end encrypted backups or no to them.
Some people need a safety net. Google should provide the option.
There needs to be an option where Google does hold a key to decrypt your backups if you choose to let it have one. Yes, that means the FBI and other three-letter agencies could get a court order for Google to hand over your data but it also means you can retrieve it if you forgot your Google account password.
I'd never use such a setting nor would I recommend it to anyone. But I'm not you and you may rather have the safety net of getting your data back in case of user error. That's one place where we are all the same; we make lots of errors. Google should expand the service and present the option in a way that informs the user of the drawbacks and benefits, then let us opt-in if we choose.
Finally, you can't use data from a newer version of Android to restore a phone running an older version. That means when the Pixel 5 comes out running Android 11 this Autumn, you can't use it and then decide you like the Galaxy S20 better and restore your data to it until it gets updated early next year. there are certainly technical reasons for this, but Google has smart people who have figured out tougher problems.
It's still great to see
Though it has a few issues that Google really needs to sort out, Android backup is a great thing to see. With no universal desktop client that can create a 1:1 backup image of your phone, Android depends on the cloud to do it all. Google is doing the right thing by having a free end-to-end encrypted backup service in place for developers to use and we benefit from it greatly.
Even with imperfections, Android backup is a great service to see.
No service will ever be perfect, and Google is often accused of releasing them long before they are ready. But in this case, Android backup is a complete package that has been independently audited and found to be pretty bulletproof. The only changes that need to happen are some of the policies about how it's used.
Get More Pixel 3a
Google Pixel 3a
Pixel 3a From $399 at Amazon Pixel 3a XL From $479 at Amazon
from Android Central - Android Forums, News, Reviews, Help and Android Wallpapers https://ift.tt/37kaDoJ
via IFTTT



Aucun commentaire:
Enregistrer un commentaire